BALTIMORE -- Police were waiting for Deon Batty when he stepped off a Baltimore City bus traveling along a commercial strip near the public Douglass Homes on Valentine’s Day three years ago.
When authorities asked Batty to empty his pockets, he pulled out a cell phone and handed it over.
An officer dialed the number of a 77-year-old woman who had been robbed of her phone and other items at gunpoint the night before. The phone in the officer’s hand rang.
The seamless chain of events baffled Batty’s public defender, Janine Meckler. How did police know he was on that particular bus? Why had they stopped him without a warrant? How did they know he had the woman’s phone?
The mystery deepened in the hours before Batty’s trial in Baltimore City Circuit Court in September 2014. As Meckler shifted through case files, she discovered something she’d never noticed in her 25 years on the job: an after-action police report from the city police’s Advanced Tactical Team. Though she’d seen after action reports, what was unusual about this one was the phrase “target phone.”
A phone call to another attorney and a Google search led Meckler to a StingRay, the common name for a cell site simulator. It is a suitcase-size device developed for the foreign battlefield that mimics a cell tower, tricking nearby mobile phones into answering it with identifying information and location data.
The Public Records Behind This Story
Capital News Service requested dozens of records from Maryland law enforcement agencies in an attempt to discover how cell site simulators were being used in the state. Some agencies were more forthcoming than others. We're sharing 35 documents we unearthed that we used to tell this story: usage logs, non-disclsoure agreements the agencies signed with the FBI in order to use the technology, purchase orders, police reports from investigations where the technology was used, court transcripts, denials of our requests for information and other documents.
Cell site simulators are among the most controversial of intelligence devices to have worked their way into the hands of law enforcement in recent years.
Because they indiscriminately scan phones while searching for their target, data from bystanders is also scooped up, dragnet-style.
Citing unusual secrecy agreements with the FBI or the need to protect an investigatory tool, most local law enforcement agencies using the equipment in Maryland refuse to answer questions about what happens to this data, or other rules governing its use.
Without this information, defense attorneys say they can’t challenge how they operate, like they can with radar equipment or even fingerprints. “We have no clue how it’s being used, whether the machine is being used properly… there’s no accountability. That’s a huge problem,” Meckler said.
The problem, said lawyers and experts in law enforcement surveillance issues, is that technology has outpaced local laws. As public disclosures about cell site simulators increased in the last year, the Departments of Justice and Homeland Security began requiring their employees for the first time to obtain search warrants before they can use their devices, with some exceptions.
Each agency also enacted rules for deleting data. Those rules include provisions that say data must be deleted as soon as a target is found, and in no less than every 30 days in cases where the equipment is used to identify unknown devices. Each also added auditing requirements.
These new federal guidelines, however, don’t apply to local law enforcement. But some states, including California, Virginia and Washington have enacted similar legislation.
“The main problem is that the police may be doing something illegal and we have to use mental gymnastics to try and uncover these secret aspects of an investigation that are never written down and turned over to us,” Jason Ricke, a Prince George’s County assistant public defender, said. “The police may be violating our clients’ rights and we will never know it.”
Although some Maryland agencies have been using the technology for at least a decade, it wasn’t until October 2014 that police in the state were required even to show probable cause to use real-time cell site location information, according to a four-month investigation by Capital News Service.
What's a Cell Site Simulator?
The military, intelligence agencies and police use cell site simulators to gather information. Mobile devices continuously scan and connect to nearby cell towers. To a mobile device, the cell site simulators are indistinguishable from a cell tower. But instead of connecting the mobile device to a mobile network, the simulators capture location and other information from the device, allowing the operator to track the mobile device owner.
Source: Heath Hardman, Social Science Research Network. Capital News Service graphic by Joey Trull.
The CNS investigation also found that police agencies in the seven counties closest to the Washington and Baltimore regions have spent at least $2.8 million on the sophisticated equipment.
At least 61 police agencies in 23 states and Washington, D.C. have deployed cell site simulators, according to the American Civil Liberties Union, which has pushed for greater oversight laws and transparency over how police use the technology.
“I would say that this shouldn’t ever be a secret,” David Rocah, senior staff attorney at ACLU of Maryland, said. “We’re not talking about catching spies. We’re talking about routine criminal investigations.”
Court records, public documents and interviews show that law enforcement agencies used their cell site simulators to set up wiretap cases, locate missing and suicidal persons and investigate homicides, assaults, drug trafficking and even robberies of gas stations and pizza deliverymen.
Among CNS’ findings:
- Maryland State Police has used its cell site simulator at least 125 times since 2012, most often in Baltimore County, which has its own cell site simulators, and in Wicomico County, on the Eastern Shore.
- Howard County has spent at least $452,000 on a cell phone tracking and jamming system that it has used at least 129 times since 2011, leading to at least 27 arrests.
- Governor’s Office of Crime Control and Prevention records show Annapolis Police received a $184,955 federal grant to buy its equipment.
- Heavily redacted records show Montgomery County Police, which obtained its equipment a decade ago, paid $260,944 in 2011 to continue its use. The county has paid an additional $222,961 since then, some of it for “upgrades/enhancements.”
- Anne Arundel County has spent more than $151,000 on its cell site simulator and maintenance agreement since 2013, according to purchase orders and other public records.
- The Prince George’s County Sheriff’s Office received a $327,000 Justice Department grant in 2009 to buy its cell site simulator system. Within a month of installing it in a vehicle in December 2010, the agency had already used it five times and captured four suspects in cases that included an armed robbery, a carjacking and three attempted murders.
SECRECY SURROUNDS TECHNOLOGY
When Janine Meckler sought more information during a hearing about how police knew her client was carrying a stolen cell phone, the assistant state’s attorney asked the judge to bar her from asking for more details about it.
“That’s when I knew I had something,” Meckler said.
The state’s attorney’s attempt to stop Meckler is similar to reasons given by police departments to deny CNS’ requests for information under the law: Secrecy necessary to conceal details of the technology from criminals that would allow them to skirt capture.
Montgomery County also invoked executive privilege to withhold records, citing “sensitive information pertinent to matters of national security.”
Montgomery County Invokes “National Security”
Montgomery County also invoked executive privilege to withhold records, citing “sensitive information pertinent to matters of national security.”
In some cases, the FBI has required local agencies to sign confidentiality agreements prohibiting them from disclosing even whether they are using the devices.
The FBI “believes that this technology is a vital tool in homeland security operations and disclosure of this technology could expose ways to subvert this investigative tool to terrorists and criminals alike,” Baltimore County Police Cpl. Shawn Vinson wrote in a response to a CNS request for information.
Non-disclosure agreements signed by some agencies and the FBI direct local police to contact the bureau so it has the opportunity to intervene to stop public disclosures about cell site simulators.
Baltimore County: Disclosure Could Help Terrorists
The FBI “believes that this technology is a vital tool in homeland security operations and disclosure of this technology could expose ways to subvert this investigative tool to terrorists and criminals alike,” Baltimore County police said in denying access to some information about the agency's use of cell site simulators.
That explains why Maryland State Police Sgt. Thomas Bonin told then-state Sen. Christopher Shank during a March 2014 hearing that he could not comment on whether or not the agency owns a StingRay, the name of the most commonly use simulator.
Maryland State Police signed its agreement with the FBI, which it released to CNS, on Feb. 12, 2012.
“Is it classified?,” Shank asked during the hearing.
“It is classified,” Bonin said.
Secrecy even surrounds the non-disclosure agreements. The FBI won’t say how many such agreements it has signed with local jurisdictions.
At least 20 agreements have become public in recent years, largely as the result of public records requests. Baltimore City police’s agreement surfaced in public court files last spring in a case against two teens charged in an armed carjacking. Anne Arundel Senior Assistant Attorney Philip Culpepper also acknowledged that county police’s agreement with the FBI.
FBI Spokesman Christopher Allen said the non-disclosures aren’t meant to prevent all discussion about the devices. The FBI doesn’t tell local police how they can use their devices either, he said.
“The goal is to protect the tradecraft capabilities of the device … with the idea of preventing countermeasures,” Allen said.
To Use Cell Site Simulators, Some Agencies Sign Non-Disclosure Agreements with FBI
Maryland State Police and Baltimore City police have both signed agreements with the FBI, limiting what they can reveal about their use of cell site simulators. Secrecy even surrounds the non-disclosure agreements. The FBI won’t say how many such agreements it has signed with local jurisdictions.
Baltimore City Non-Disclosure Agreement Maryland State Police Non-Disclosure AgreementBut sometimes prosecutors have decided to offer plea deals in otherwise strong cases rather than disclose the use of cell site simulators.
When a Prince George’s County public defender questioned whether U.S. Marshals, accompanied by county police, had used a cell site simulator to locate his client in a Laurel apartment in January 2015, his response was a plea deal.
Assistant Public Defender Ricke said it looked to him like the marshals had picked Stephon Summers “out of thin air.”
Summers is serving seven years for violating probation in addition to a concurrent five years for a weapons violation he was charged with when police found him in January 2015. Without the plea, he faced up to 25 years, Ricke said.
“That’s something that law enforcement has to account for, that they’re putting secrecy ahead of public safety,” said the ACLU’s David Rocah. “You cannot say that these things are critical to public safety and then sell out public safety in the same breath.”
PRIVACY CONCERNS ABOUND
A summary of Annapolis Police’s cell phone interceptor program says it “allows the department to locate and apprehend violent offenders, track persons of interest, monitor crowds when intelligence suggests threats; and intercept signals that could activate devices.”
Annapolis received a $184,965 Justice Department grant for that program in 2010, according to Governor’s Office of Crime Control and Prevention documents.
Little is known about the data local police agencies are gathering and how it is handled.
“If the agency doesn’t have a policy in place to delete that data, who knows what they’re doing with it?” said Jennifer Lynch, a senior staff attorney with the non-profit Electronic Frontier Foundation.
Brian Owsley, a former federal magistrate from Texas who has researched the technology, said Annapolis’ admission “further bolsters that they’re big government coming in, they’re watching everyone.”
Annapolis Police declined to comment.
Some agencies have been more willing to talk about what they don’t do. Maryland State Police said it does not retain third-party data and does not use its devices for crowd monitoring.
Baltimore County and Anne Arundel County both said they don’t store any data. Anne Arundel added that it does not intercept the content of communications.
Other police agencies, including those in Anne Arundel, Howard and Prince George’s declined or did not respond to interview requests. Sheriff’s offices in Prince George’s and Harford County also did not respond.
Baltimore City Police’s acknowledgement, first reported by The Baltimore Sun, that it had used its StingRay in 4,300 cases going back to 2007 helped fuel a national conversation about the need to balance public safety while protecting bystander privacy.
Baltimore defense attorneys are now seeking additional information about those cases in an attempt to overturn them.
Former Harford County Sheriff Jesse Bane said his office conducted internal audits of the device’s use and retained only data critical to an investigation. He didn’t rule out that other information wasn’t kept.
“If we had a series of telephone numbers that were linked to drug dealers, we were going to hang on to those numbers,” said Bane, who lost his bid for sheriff in 2014 and now works as the town administrator of Bel Air.
Bane reviewed documents detailing the county’s purchase of more than $400,000 in surveillance equipment in 2011, which he approved. The county bought the equipment using a Department of Homeland Security Urban Areas Security Initiative grant, according to the documents. It spent another $52,000 in June 2014 on equipment upgrades.
The grant is meant to enhance regional preparedness and capabilities against terrorism and other threats in high-risk, high-density areas, according to DHS.
But Bane said the county purchased its equipment to help its drug enforcement efforts. He estimated officers used the equipment—which he said was installed in a vehicle—about once a month. He could not provide specifics regarding how effective the cell site simulator was in locating targets.
“I wanted to stop the flow of drugs into the county as much as I could,” Bane said. “It’s very difficult to do if you don’t have the technology.”
Harford County Sheriff’s officers worked with the state’s attorney’s office to draft court orders when they used their cell site simulator, Bane said.
“I wanted to make sure we weren’t getting cases dismissed on technicalities,” Bane said.
LEGAL QUESTIONS ARISE FROM USE
The law governing use of cell site location information in Maryland changed in October 2014. It raised the burden of proof and required a court order before law enforcement could conduct real-time tracking, except in cases where a device’s owner had approved it or in cases of life or death. Even then, police must now retroactively get a court order within 48 hours, the law states.
Legislation introduced in February would have tightened the rules even further by requiring law enforcement agencies to tell the courts when they planned to use a cell site simulator. The bill also would have placed limits on data collection and required annual reporting by police agencies. It failed to make it out of committee.
But a 74-page state Court of Special Appeals decision issued March 30 is being hailed as the first of its kind in the country by civil liberties experts. The order upheld a ruling by a Baltimore City Circuit Court judge who said police violated Kerron Andrews’ Fourth Amendment rights when they used a StingRay upgrade called Hailstorm to locate him without a warrant in May 2014. Police deployed the Hailstorm to find Andrews, who is accused of attempted murder, after obtaining a pen register/trap and trace order. The orders, which require less than probable cause, have long allowed police to obtain lists of numbers called and received by a user from phone companies.
The court called the city police’s conduct in the case misleading and “unconstitutionally intrusive” and upheld the lower court’s order throwing out evidence gathered by the Hailstorm.
The three-judge panel also took aim at the non-disclosure agreements between law enforcement and the FBI.
“A nondisclosure agreement that prevents law enforcement from providing details sufficient to assure the court that a novel method of conducting a search is a reasonable intrusion made in a proper manner and justified by the circumstances obstructs the court’s ability to make the necessary constitutional appraisal,” the justices said.
Maryland's Second-Highest Court Criticizes Use of Cell Site Simulators, Non-Disclosure Agreements
The Maryland Court of Special Appeals found that Baltimore police violated a man's rights when they used a cell site simulator to locate him without a warrant, calling city police's conduct “unconstitutionally intrusive.” The court also criticized non-disclosure agreements between law enforcement and the FBI.
David Nitkin, who until last month was a spokesman for Maryland Attorney General Brian Frosh, said the office was evaluating the ruling and considering its options.
A spokesman for Maryland Attorney General Brian Frosh said earlier this year that the office was evaluating the ruling and considering its options.
Rocah, of the ACLU, said the court’s decision could mean a reopening of scores of cases across the state, not just in Baltimore.
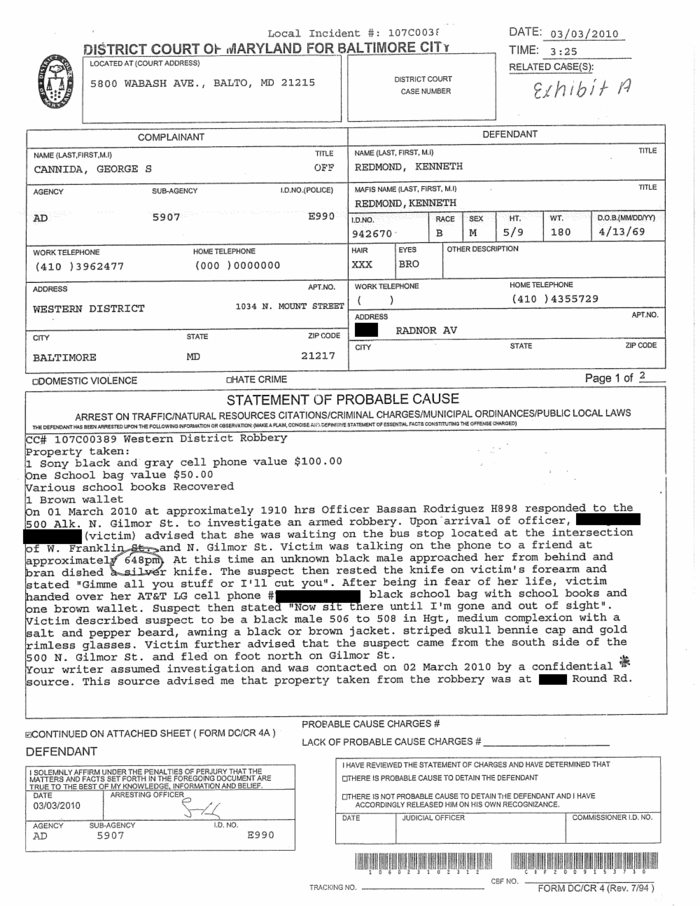
Even then, defense attorneys may face an insurmountable challenge. Given the hidden history of cell site simulator use in Maryland, it’s near impossible to know in how many cases police have used the devices, Rocah said. Defense attorneys have said withholding discovery before a trial has been an on-going concern. To add another challenge, the attorneys say police have obscured the use of simulators by using vague language in court documents, forcing them to read between the lines. In at least one case, a device was referred to as a “confidential source” in charging documents.
Technology Called a "Confidential Source"
Attorneys say police have obscured the use of simulators by using vague language in court documents, forcing them to read between the lines. In this case, a device was referred to as a “confidential source” in charging documents.
Text messages between two Montgomery County Police detectives made public defender Ron Gottlieb question if a cell site simulator was used to track Mauricio Morales-Caceres, who was convicted last week in a December 2014 homicide, according to Gottlieb.
Montgomery County Assistant State’s Attorney Douglas Wink acknowledged during a November hearing that a cell site was used in the case but said there was no additional documentation.
“It should be disclosed upfront in discovery under the rules,” Gottlieb said during the hearing. “I had to ask for that.”
HOW CELL SITE SIMULATORS WORK
Cell site simulators were initially used overseas by intelligence agencies and federal law enforcement. Homeland Security agencies including the Secret Service and Immigration and Customs Enforcement also now use the devices, as does the Internal Revenue Service.
As the technology improved and spread through federal agencies, local and state agencies learned of them too. DHS and DOJ officials have said that domestically, their devices only scoop up metadata. They do not gather content, like emails or text messages.
Cell site simulators rely on signal strength and direction finding to locate a target device, Heath Hardman, a former signals analyst for the U.S. Marines Corps, said.
Hardman used the devices while deployed in Iraq and Afghanistan in 2007 and 2008 and also taught troops how to operate them. If done incorrectly an operator could kick users off a network, forcing them to power their phone off and on before reconnecting, he said.
Or, if an operator broadcasts too broad of a signal, it can overload a network with too many devices looking to jump from one cell tower to another.
“It’s a little bit of an art and a science,” Hardman said.
For these reasons, the Federal Communications Commission must authorize a manufacturer to sell the device. But that authorization only signifies that the equipment meets FCC standards to control radio frequency interference, FCC officials said.
Melbourne, Fla.-based Harris Corp produces the StingRay, which has become a generic name for similar devices. Harris spokesman Jim Burke said it is company policy not to comment on its product. A spokeswoman for Germantown-based Digital Receiver Technologies, Inc., a Boeing subsidiary that produces a cell site simulator referred to as DRTbox, also declined to comment.
HOW POLICE USE THE DEVICES
Many agencies say national security and the need to protect an investigatory tool prevents them from talking about cell site simulators. That extends to the cases themselves. It’s unclear how many cases had links to national security. Logs released by some agencies do not explicitly cite national security but instead include violent crimes such as homicides and rape; others were more routine crimes, including burglaries, assaults and auto theft.
One case involved the theft of chicken wings.
“It’s supposed to be used for terrorism,” Meckler, the Baltimore public defender, said. “It’s not being used for the purpose for which it’s being designed.”
Montgomery County Police spokesman Capt. Paul Starks said the agency used its cell site simulator 80 times from April 1, 2015 through March 31. The number indicates uses, not individual cases, he said. About 30 percent, or 24, of those uses were for homicides and another three were kidnappings, Starks said.
The county may also use its cell site simulators to find critically missing people, like runaway children or those with mental, physical or emotional disabilities but the agency doesn’t track those, Starks said. The agency does not track how many times it successfully locates its target, Starks said. County police usually obtain a court order before using its devices or seek one soon afterwards, he said.
“We absolutely use it to go after the worst criminals or the worst criminal offenses,” Starks said. “We use it for violent felonies and do not use it for minor crimes and property crimes.”
Baltimore County Police spokeswoman Elise Armacost said the tool has been effective in local crimes. They successfully located 63 of 72 targets they sought using the device in 2015, according to a log released to CNS. In 2014, county police located 110 of the 119 targets they sought while using the device. The investigative unit that handles the device got 99 requests from county police to use it in 2015. In 2014, the unit got 150 requests, according to county logs.
The “technology is useful at helping us find missing persons and wanted suspects, thus furthering our public safety mission,” Armacost said in an email. “We use this equipment only when there is law enforcement need and probable cause.”
Success rates in other counties were not as high.
Since 2011, Howard County has investigated more drug cases with its devices than any other type of crime. Of the 41 drug cases, which represent a little more than 30 percent of the investigations, police made only one arrest. Several of those cases were to develop targets for wiretaps, according to a log released to CNS.
Howard police also used the device in suicides, kidnappings and in at least three cases where threats were made to public officials.
Annapolis’ log shows police located their target in seven of the 17 cases in which the equipment was used since late 2011.
But Annapolis Police couldn’t find their target in the case of a Pizza Boli’s employee who reported being robbed of 15 chicken wings and three subs while out on delivery in March. In that case, police got a court order, according to the police log.
The value of the wings and subs totaled $56.77.
Ricke, the Prince George’s County public defender, still questions the use of an invasive surveillance device in tracking his client, Summers.
“He’s not a terrorist, he’s just a kid from the neighborhood,” Ricke said.
Jennifer Lynch, of the Electronic Frontier Foundation, did not know of any cases in which local police had uncovered terrorism using their cell site simulators.
“I don’t think its happened at all,” she said
NATIONAL SECURITY IN BALTIMORE COURT
Deon Batty wasn’t accused of terrorism. He faced burglary and robbery charges after police found him with the 77-year-old’s stolen cell phone when he stepped off a Baltimore bus holding a Valentine’s gift.
In court, Meckler moved to suppress the phone as evidence. It was a lark, she said.
“I never expected it to get anywhere,” Meckler said.
But during questioning, Baltimore City Circuit Court Judge Barry G. Williams threw the phone evidence out after Sgt. Scott Danielczyk refused to answer how it led police to stop Batty.
“It kind of goes into Homeland Security issues, your honor,” Danielczyk told the judge.
“OK, if it goes into Homeland Security issues, the phone doesn’t come in,” Williams said. Batty’s stop by police amounted to a warrantless search, he ruled.
A jury hung 11-1 in the case. Batty got a deal for time served and pled to a second-degree assault charge. He’s currently serving out the rest of a probation violation charge at Dorsey Run Correctional Facility in Jessup.
Meckler said she never determined from city police that they used StingRay to track Batty down. But a February 13, 2013 entry in a city log obtained by CNS confirms it.
“I have a right to know why my client is stopped,” Meckler said in a recent interview. “You can’t just come in here carte blanche, ‘Oh, it’s national security.’”